Page 1 of 5 Knowledge Center
Transcription
Page 1 of 5 Knowledge Center
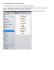
CTX116557 - How to decrypt SSL and TLS traffic using Wireshark - Citrix Knowledge ... Knowledge Center Alerts Communities Support Forums Page 1 of 5 Blogs K N O W L E D G E C E N T E R Sign in How to decrypt SSL and TLS traffic using Wireshark Document ID: CTX116557 / Created On: Mar 14, 2008 / Updated On: Apr 9, 2008 Average Rating: View products this document applies to Summary This article describes how to decrypt SSL and TLS traffic using the Wireshark Network Protocol Analyser. Requirements • An understanding and general knowledge of: – Network Traces – Networking, TCP/IP and SSL/TLS protocols – Certificates and the use of Public & Private Keys – The Wireshark Network Protocol Analyser • Wireshark software compiled with SSL decryption support • Decrypted private key of the server or appliance in PKCS#8 PEM format (RSA) Background In Wireshark, the SSL dissector is fully functional and supports advanced features such as decryption of SSL, if the encryption key is provided. This is useful when troubleshooting Citrix products that use SSL or TLS encryption. Procedure Wireshark Settings 1. Start Wireshark and open the network capture (encrypted SSL should look like the screenshot below). http://support.citrix.com/article/CTX116557 6/2/2011 CTX116557 - How to decrypt SSL and TLS traffic using Wireshark - Citrix Knowledge ... Page 2 of 5 2. From the top menu select Edit > Preferences. 3. When the Preferences window opens, expand Protocols. http://support.citrix.com/article/CTX116557 6/2/2011 CTX116557 - How to decrypt SSL and TLS traffic using Wireshark - Citrix Knowledge ... Page 3 of 5 4. Scroll down and select SSL. 5. In the space labeled RSA keys list, provide the following information in the format <ip>,<port>,<protocol>,<key_file_name> (see also the screenshot above). Where: <ip> is the IP Address of the server / appliance with the private key <port> is usually 443 for SSL/TLS <protocol> is usually HTTP <key_file_name> is the location and file name of the private key Note: There are no spaces between the colons. Also, using semicolons to separate the entries, a list of private RSA keys can be entered and used for decryption. “<ip>,<port>,<protocol>,<key_file_name>;<ip>,<port>,<protocol>,<key_file_name>;<ip>,<port>,<protocol>,<key_file_name>” 6. In the space labeled SSL debug file provide a location and file name for a debug file. http://support.citrix.com/article/CTX116557 6/2/2011 CTX116557 - How to decrypt SSL and TLS traffic using Wireshark - Citrix Knowledge ... Page 4 of 5 7. Select OK 8. The SSL traffic should now be decrypted (decrypted SSL should look like the screenshot below). Private Key Format Wireshark can decrypt SSL traffic as long as you have the private key. The private key has to be in a decrypted PKCS#8 PEM format (RSA) format. You can open and look inside your key file. If it is in binary, then it is likely to be in a DER format, which cannot be used with Wireshark. You can use OpenSSL to convert the key. For example, converting a PKCS#8 DER key to a decrypted PKCS#8 PEM format (RSA) key, at the $ prompt enter the following command: openssl pkcs8 -nocrypt -in der.key -informat DER -out pem.key -outformat PEM Where: der.key is the file name and path to the DER key file pem.key is the file name and path to the PEM key file output The Decrypted PKCS#8 PEM format (RSA) key should look similar to this: Notice that the key begins with: -----BEGIN RSA PRIVATE KEY----- http://support.citrix.com/article/CTX116557 6/2/2011 CTX116557 - How to decrypt SSL and TLS traffic using Wireshark - Citrix Knowledge ... Page 5 of 5 If it begins with: -----BEGIN ENCRYPTED PRIVATE KEY----Then the key is encrypted and needs to be decrypted with the right passphrase. You can use OpenSSL to do this. 1. At the $ prompt, enter the command: openssl rsa If you enter this command without arguments, you are prompted as follows: read RSA key 2. Enter the name of the key file to be decrypted. You can enter the openssl rsa command with arguments if you know the name of the private key and the decrypted PEM file. For example, if the private key filename is myprivkey.pvk and the decrypted filename is keyout.pem, the command is: openssl rsa –in myprivkeypvk -out keyout.pem More Information Wireshark Website http://www.wireshark.org/ SSL - The Wireshark Wiki http://wiki.wireshark.org/SSL Wireshark - Display Filter Reference: Secure Socket Layer http://www.wireshark.org/docs/dfref/s/ssl.html Open SSL Website http://www.openssl.org/docs/apps/rsa.html#EXAMPLES OpenSSL for Windows - SourceForge Website http://sourceforge.net/project/showfiles.php?group_id=23617&release_id=4880 This document applies to: Access Gateway 4.5 Advanced Edition Access Gateway 4.5 Standard Edition Access Gateway 7.0 Enterprise Edition Access Gateway 8.0 Enterprise Edition Access Gateway 8.1 Enterprise Edition Feature Pack 1 for Presentation Server 4.5 Presentation Server 4.0 for Microsoft Windows 2003 Presentation Server 4.5 for Windows Server 2003 Presentation Server 4.5 for Windows Server 2003 x64 Edition Web Interface 4.5 for Presentation Server Web Interface 4.6 for Presentation Server XenApp 5.0 for Windows Server 2003 x86 ©1999-2011 Citrix Systems, Inc. All rights reserved. http://support.citrix.com/article/CTX116557 6/2/2011