Using Prim`s Algorithm
Transcription
Using Prim`s Algorithm
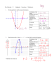
Example: An Undirected, Weighted Graph 1 8 4 0 7 2 3 9 2 8 11 4 14 4 7 8 Class #38: Undirected Weighted Graphs: Connectivity and MSTs 6 7 ! Software Design III (CS 340): M. Allen, 29 Apr. 15 1 6 ! ∞ 3. a) b) c) ! 1 0 0 Guaranteed to work for any weighted, undirected, and connected graph (i.e., with positive or negative edge-weights). Software Design III (CS 340)! 3! 2! ∞ 7 2 3 ∞ 9 2 8 ∞ 11 4 14 4 ∞ 7 Choose a vertex v1 with lowest key value that is not already in MST. Add vertex v1 to tree, connecting it via the lowest-weight edge it has to a vertex already in the tree (if MST not empty, this must exist, due to next step). For each neighbor v2 of v1, if v2 is not already in the tree, set key(v2 )= min(key(v2), weight(v1, v2) Wednesday, 29 Apr. 2015! 8 4 Each vertex begins with default key-value = ∞ Some starting vertex gets key-value = 0 Repeat until every vertex is chosen: 2. Software Design III (CS 340)! Using Prim’s Algorithm We can generate an MST in a connected, undirected graph in a greedy manner: 1. 5 2 This graph is connected: each vertex can be reached from every other one by at least one path Wednesday, 29 Apr. 2015! Minimum Spanning Trees: Prim’s Algorithm 10 8 6 7 ∞ ! 1 6 ∞ 10 2 5 ∞ We start with keys assigned to each vertex; we can pick any one we like to be the 0-key (starting) node. Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 4! 1 Using Prim’s Algorithm ∞ 1 8 4 0 0 Using Prim’s Algorithm ∞ 4 7 2 3 ∞ 8 ∞ 4 9 2 11 1 4 14 0 0 4 ∞ 6 1 6 ∞ 10 8 ∞ 11 8 Wednesday, 29 Apr. 2015! 7 Software Design III (CS 340)! 8 4 0 0 5! 3 ∞ 1 4 ∞ 10 5 ∞ 2 Software Design III (CS 340)! 4 14 8 4 9 0 0 4 ∞ 6 1 6 ∞ 10 8 7 2 6! 3 ∞ 9 2 8 ∞ 11 2 8 5 ∞ 4 14 4 ∞ Software Design III (CS 340)! 6 7 8 We now choose the next-lowest node that is connected to the MST, and add it, and its connecting edge. Wednesday, 29 Apr. 2015! 14 7 8 ! 6 ∞ Wednesday, 29 Apr. 2015! 7 7 4 Since we have added this node, we update all its neighbors to have new key values (the minimum of their current values, and the edgeweight connecting them to the tree node we just added) ! 4 7 2 8 ∞ 8 9 Using Prim’s Algorithm ∞ 2 11 1 8 Using Prim’s Algorithm 1 3 ∞ 6 5 ∞ 2 We then begin by choosing the starting node (lowest key) and adding it to the tree by itself. 4 7 2 7 8 ! ∞ 2 7 7 ∞ 8 7! ! ! 1 6 ∞ 10 2 5 ∞ When we update node weights now, we have a choice between two nodes with key-value 8. The algorithm works no matter which we choose. Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 8! 2 Using Prim’s Algorithm 4 1 8 4 0 0 Using Prim’s Algorithm 8 4 7 2 3 ∞ 8 7 4 14 0 0 4 ∞ ! 6 1 6 1 10 8 7 11 8 5 ∞ 2 Wednesday, 29 Apr. 2015! 7 Software Design III (CS 340)! 8 4 0 0 9 4 14 4 ∞ 7 2 8 2 1 6 1 10 2 5 ∞ The next vertex to choose is node 6, which means that we will update not only node 5, but change the key for node 8 again (from 7 to 6) since we have found a lighter edge to it from the MST. Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 10! Using Prim’s Algorithm 4 3 7 1 4 14 3 9 2 0 4 9 7 2 4 9 2 11 ! 9! Using Prim’s Algorithm 1 3 ∞ 6 8 Supposing we choose node 7, we add it and its minimal connecting edge to the MST, and then update key-values for each of its non-MST neighbors. 4 7 2 7 8 7 8 2 7 8 8 4 9 2 11 1 8 4 4 7 8 6 7 8 ! ! 1 6 1 10 2 8 5 2 7 We continue until all vertices have been added to the MST. At this point, the red edges alone comprise a tree of total weight 37 units (down from the total weight of the original network, which was 93 units). Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 11! ! 1 6 2 5 When we are done, we again have an undirected and connected graph, but with only one path from any node to any other, and minimal possible weight. Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 12! 3 Using Prim’s Algorithm 1 8 4 7 2 ! 3 8 1. 9 2 This edge instead. 0 Implementing Prim’s Algorithm: One way 4 4 8 Not this edge. ! 7 1 6 2 5 2. Create one such object for each vertex, and place them into a list (using either a linked or array-based implementation). 3. Loop over the list: each loop chooses a minimal vertex object: one with lowest key that is not already in the MST. Loop over all vertices, one by one. 4. Add that vertex to the MST. Adjust keys of neighboring vertices downward. Stop when every vertex has been included. Repeat once per vertex. Depending upon the network, as we saw above (slides 8 & 9), there are sometimes ties. If we broke ties differently, choosing node 2 before node 7, we would get a different MST, but one with the same minimal weight (37). Wednesday, 29 Apr. 2015! Software Design III (CS 340)! For number of vertices V, this method will repeat V times, looping O(V ) times on each repetition, giving run-time that is O(V 2) 13! Prim’s Algorithm: Another way Here is one basic approach: Create a simple data-structure to store information about a single vertex: (a) which one it actually is, (b) its key-value, and (c) whether it is already in the MST. Wednesday, 29 Apr. 2015! ! 2. Create one such object for each vertex, and place them into a priority queue (ordered by key-value, ascending). 2. Create one such object for each vertex, and place them into a priority queue (ordered by key-value, ascending). 3. Choose the highest priority object in queue: one with lowest key that is not already in the MST. 3. Choose the highest priority object in queue: one with lowest key that is not already in the MST. 4. Adjust keys of neighboring vertices downward. Stop when every vertex has been included. 4. Adjust keys of neighboring vertices downward. Stop when every vertex has been included. 1. 1. Get 1st vertex: O(1) time. Repeat once per vertex. First-pass analysis: For number of vertices V, this appears to repeat V times, doing O(1) work on each repetition, giving run-time that is O(V ) Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 14! A Closer Look Here is another approach: Create a simple data-structure to store information about a single vertex: (a) which one it actually is, (b) its key-value, and (c) whether it is already in the MST. ! Software Design III (CS 340)! 15! Here is another approach: Create a simple data-structure to store information about a single vertex: (a) which one it actually is, (b) its key-value, and (c) whether it is already in the MST. Problem: when we adjust the keys of elements already in the queue, does this actually re-order queue at all? Answer: In a basic Priority Queue, the answer is NO. Thus we have to add in the work it takes to do this re-ordering. Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 16! 4 Solutions to the Problem ! 1. 2. 3. Final Analysis of Prim’s Algorithm A bad approach: when we need to adjust the weight on a vertex: Search for it in the queue. Remove it. Re-insert it so that it ends up in proper order. For choice between basic list and basic priority queue: 1. If graph is sparse (few edges): queue for O(V log V ) ! 2. Why this is bad: For V vertices, search takes O(V ), and re-insert takes O( log V ), so this process takes O(V log V ) and whole algorithm becomes O(V2 log V ), which is worse than original O(V2 ). A better approach: store edges in queue, not vertices, and each time we update a vertex, we add a new copy of an edge, with a lower key-weight. ! ! Efficiency now depends upon how many edges there are. Complexity: for E edges, insert of copy is O( log E ) , and we loop E times overall. Best-case: For V vertices, we have O(V ) edges, so: O(V log V ) < O(V2 ). Worst-case: For V vertices, we have O(V2 ) edges, so: O(V2 log V2 ) > O(V2 ). Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 17! ! ! If graph is dense (many edges): list for O(V2 ) More complex data structures, like Fibonacci Heaps, can re-order after keys are modified in amortized O(1) time If we can implement such a structure (which has its own costs in development time, since they are complicated to get right), then the heap/queue approach would be the most efficient in every case, allowing overall time O(V ) Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 18! This Week and Next ! Meetings: Normal schedule this week ! Reading: Chapter 09 ! Homework 05: due Friday, 08 May, 5:00 PM ! Office Hours: Wing 210 ! ! Monday & Tuesday: 3:00–5:00 Thursday: 2:00–3:30 Wednesday, 29 Apr. 2015! Software Design III (CS 340)! 19! 5