RSA Monthly Online Fraud Report -
Transcription
RSA Monthly Online Fraud Report -
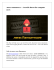
RANSOMWARE: INFECT ME NOT June 2012 RSA researchers have been following ransomware campaigns and ransomware Trojan attack waves and have recently analyzed a new variant that holds infected PCs hostage until their owners make a €100 payment to the botmaster. The more interesting part of this malware’s operations is its location – what appears to be a server most likely orchestrating botnet monetization and affiliate infections deals. Ransomware is the type of malware that can infect a PC and then lock the user’s data most commonly by encrypting files or by injecting a rogue MBR (master boot record) to the system’s start-up routine. Ransomware can come as standalone malicious code or coupled with other malware. This type of malicious campaign has been on the rise and are ever popular, with many recent cases combining banking Trojans with ransomware. While the user’s files are typically locked until the ransom is paid, the victim is still free to browse the Internet, thus allowing the banking Trojan to continue collecting information on the victim uninterrupted. The Trojan involved in the cases studied by RSA is a ransomware that begins by checking for the future victim’s geo-location and adapting a ransom page to the local language for thirteen different countries. The fact that this malware aims at 13 specific countries may seem targeted enough at first sight, but it is only the case of one variant – if this malware is shared or sold with other criminals, they could easily adapt it to their own targets. FRAUD REPORT ANALYSIS OF A RANSOMWARE KIT The Trojan encrypts the end-user’s personal data (documents, photographs, etc.) and then demands they pay to receive an unlock code for their system. Once the user pays with a valid PIN/voucher – the botmaster actually sends back an unlock command and releases the hold on the PC. Unlocking the PC is a rare occurrence in cybercrime. Most ransomware botmasters do not have any set-up designed to unlock the PC. Of course, this case is not an indication to an honorable thief, but rather to a cybercriminal planning to possibly re-monetize that bot in the future. Researchers at RSA Trojan Labs obtained and ran the malware’s executable binary and confirmed that although it begins with typical ransomware deployment, it promptly moves to checking the victim’s geographic location. In order to define the location of the infected machine, the malware uses a Windows function called GetUserGeoID (on the user’s level this can be accessed via Control Panel->Regional and Language Options->Location). Although this method is simple, it is efficient and rarely deployed by other similar Trojans. The malware converts the country name to a unique 3-character ID and then uses that code in its GET request to the C&C server for a customized ransom message to the victim. The Trojan receives back the country-specific page on the fly. Unlike other ransomware variants, this malware downloads an archived file (PK header) containing one main HTML page, JS/CSS files and the ransom-demanding image presented to the victim. RSA researchers were able to recognize 13 different ransom kits available for this Trojan. All kits are located in the same folder, where some countries have two different types of images that can be downloaded and used by the ransomware (in cases when more than one language is spoken in that country, such as Belgium). After the ransomware kit infected the PC, it was downloaded and unpacked locally. This is the point at which the Trojan begins its primary communication with the botmaster’s remote server. The communication includes three main purposes: –– Inform the botmaster of the addition of a new bot, send infected machine’s IP address (and then used to define the infected PC’s physical location) –– Obtain a blacklist of potentially fake prepaid card/voucher numbers defined by the botmaster –– Ping the botmaster to use the C&C as a drop for the coming ransom payment (in the shape of a card PIN/voucher number) This Trojan also makes a few copies of itself and saves them under different names locally on the infected PC. RANSOMWARE’S CYBERCRIME SERVER SIDE Much like other Trojans, this ransomware is managed via server side scripts on the botmaster’s resources. The variant analyzed in this case used four resources, all of which were located on the same physical server, using two different IP addresses held with a Russian-based ISP – typical for the vast majority of ransomware. RSA was able to deduce that the ransomware analyzed is actually part of a larger cybercrime operation. The botmasters behind this malware variant are clearly bot-herding and monetizing their botnets using a loader Trojan, banking Trojans and ransomware variants. The server hosting the ransomware has proven to also be a drop zone for stolen credentials amounting to well over €80,000. page 2 EVEN MORE RANSOMWARE An additional type of ransomware found on the same server was targeting German consumers, instructing victims to pay €100 for an unlock code. The message informed the victim that their system was infected due to infringement and is now locked using strong AES-256 encryption. The locker claims that the only Anti-Virus software that can clean the system is “Antivirus System Repair v2.2”/ “Antivirus Harddisk Repair v2.2”, the fake name used by the cybercriminals. Infected PC owners are told they are to purchase a prepaid card/voucher for €100 and make the payment to: [email protected]. Open source search results for this malware and email show that it was used vastly in recent ransomware infection campaigns. Ransom Message Presented to Users of Infected Machine, Demanding €100 Payment for Fake AV CONCLUSION Ransomware has been gaining speed among cybercriminals and bot-herders, likely because this extortion method works and keeps paying off, as victims believe that if they pay, their system will be unlocked. With ransom amounts averaging €100, it seems as though botmasters behind these scams keep the fee relatively low, possibly so that the victim may prefer to pay it in hopes of releasing the hold on their PC rather than contact a support professional. Another factor keeping victims quiet are typical ransomware accusations, including things such as software and music infringement. It is very possible that users do not know they were infected by malware and are not keen on contacting someone about it, thus allowing this type of malware to enjoy its continued popularity. page 3 In May 2012, phishing volume increased by seven percent, with a total of 37,878 global attacks identified by RSA. The bulk of the increase observed in the past two months is a result of highly targeted phishing campaigns launched against a small number of financial institutions. 38970 40000 37878 35558 35000 30000 25191 25000 23097 29974 28365 26907 Source: RSA Anti-Fraud Command Center Phishing Attacks per Month 24019 22516 21119 21030 19141 20000 15000 10000 5000 376 351 321 300 313 303 281 281 Jan 12 Feb 12 300 298 288 298 Source: RSA Anti-Fraud Command Center 349 350 256 Number of Brands Attacked The number of brands targeted by phishing attacks throughout May increased by four percent, and fifty percent endured less than five attacks. May 12 Apr 12 Mar 12 Feb 12 Jan 12 Dec 11 Nov 11 Oct 11 Sept 11 Aug 11 Jul 11 Jun 11 400 May 11 0 250 200 150 100 50 0 May 12 Apr 12 Mar 12 Dec 11 Nov 11 Oct 11 Sept 11 Aug 11 Jul 11 Jun 11 May 11 page 4 US Bank Types Attacked 12% 11% 10% 19% 6% 14% 9% 6% 19% 3% 12% 9% 16% 76% 69% 67% 61% 69% 74% 75% Aug 11 Sept 11 Oct 11 Nov 11 13% 21% 30% 86% 68% 76% 58% 82% 62% May 12 12% Apr 12 25% Mar 12 20% Feb 12 23% Jan 12 20% 20% Dec 11 12% Jul 11 80 Jun 11 Phishing attacks against U.S. nationwide bank brands decreased by 20 percent while credit unions saw a 13 percent increase in phishing volume in May. 7% 11% 18% 60 40 20 0 Source: RSA Anti-Fraud Command Center 100 May 11 Brazil 2% a Australia South Korea Canada China Germany Colombia 1% UK Canada 3% Top Countries by Attack Volume After being targeted by 28 percent of worldwide attacks in April, Canada saw a huge drop in attack volume in May to just three percent. The UK remains the most heavily targeted country for the third consecutive month, enduring more than 60 percent of global phishing volume in May. 42 Other Countries 6% United Kingdom 63% U.S. 25% page 5 a US ChinaChina 3% S Africa France 3% Italy Canada Netherlands India Bras Italy 3% Canada 3% Top Countries by Attacked Brands India 4% The countries with the most attacked brands in May were the U.S., UK, and Australia, accounting for 47 percent of all phishing attacks. Brands in Brazil, India, Canada, China, France and Italy also continue to remain highly targeted by phishing. Brazil 4% 38 Other Countries 33% Australia 5% United Kingdom 11% U.S. 31% Portugal 1% France 1% a US Spain 2% S Africa China Italy Canada Netherlands 1% Netherlands India Japan 2% Canada 2% Top Hosting Countries The U.S. saw an increase of ten percent in the number of phishing attacks it hosted in May – increasing to 66 percent, or two out of every three attacks. Brazil also remained a top host with nine percent and Germany with four percent. U.K. 2% Germany 4% Brazil 9% U.S. 66% 60 Other Countries 10% page 6 Bra CONTACT US To learn more about how RSA products, services, and solutions help solve your business and IT challenges contact your local representative or authorized reseller – or visit us at www.emc.com/rsa www.emc.com/rsa ©2012 EMC Corporation. EMC, RSA, the RSA logo, and FraudAction are trademarks or registered trademarks of EMC Corporation in the U.S. and/or other countries. All other trademarks mentioned are the property of their respective holders. JUN RPT 0612